One of the reasons that individuals have been reluctant to put resources into digital money is a result of security gambles. Dissimilar to FDIC-guaranteed ledgers, cryptographic money is unregulated by most governments so you might not have lawful recourse.
Although there are risks involved with using digital wallets or conducting any online transactions by designating the saving of our account or card information on an external party platform, we may avoid these errors and protect ourselves from being hacked by taking a few cautious precautions.
What Industries Utilize Digital Wallets?
Digital wallets are programmes designed to expand access to digital goods by utilizing the capabilities of mobile devices. Since digital wallets may be used without carrying tangible forms of currency, losing your pocket wallet is no longer a problem if you have one.
You may use your sophisticated wallet once it is set up to make online or contactless payments, purchase retail tickets and coupons, and much more. There are many other digital wallets available, but two of the more well-known ones are Apple Wallet and Google Wallet.
Who Uses Electronic Wallets?
You are not required to use a digital wallet. But, since you don’t need to carry about credit and check cards, they provide a useful way to pay for your purchases. This improves card security further since if you don’t carry your cards, you can’t lose them.
Read: Did You Know- 14 Bitcoin Facts
Which Company Is Heading The Run For Digi Wallets?
Only users of iPhones, iPads, and Mac watches can access the improved Apple Pay digital software. It enables customers to swap items for both online and in-store purchases. Customers can hold their phones open and close to a functional retail location framework for in-store exchanges. With its ease of use, the Apple Pay application enables a reliable and secure manner of payments.
An addition to PayPal’s standard procedures is the PayPal One TouchTM application. By enabling users to skip the login screen and do away with the need to input passwords, it enables customers to make payments or change reserves more quickly. Work using PayPal’s flexible wallet application on a desktop, laptop, or tablet as well.
How Often Are E-Wallets Hacked?
The most current worst case scenario for e-wallets, which are routinely targeted by hackers, is for cryptocurrency wallets. Attackers can make more money off of cryptocurrencies as more people invest in it. From the start of the outbreak in April 2020, there have been roughly a dozen attacks and almost $3 billion worth of cryptocurrency have been taken from exchanges. Hackers have numerous different methods for obtaining cryptocurrencies, including stealing or guessing your password, breaking into an exchange platform, phishing for information, and more.
Recommended: Demystifying AR/VR Technology In Healthcare Domain
How to Protect Your Crypto Wallet: 8 Steps
- Use a cold wallet first
Hot wallets are internet-connected wallets like Exodus and MetaMask while Cold wallets are Offline wallets that are not online, like a USB drive.
2. Employ two-factor authentication (2FA)
A second layer of security is added to your record by 2FA. When someone tries to sign in, a message or email with a check code is sent to you. Hackers will find it more difficult to access your record thanks to this added step. They would need this check code, so they might call and make an effort to convince you to provide it to them. Never divulge your 2FA code, One Time Password (OTP), or any other private verification code to a third party. The crypto exchange doesn’t request certifications over the phone.
3. Save your seed phrase in a secure location.
A wallet provider like MetaMask will produce a collection of 12 to 24 random phrases as a “seed phrase.” This seed phrase needs to go in the exact identical grouping that you see while marking up. Unfortunately, there is no reliable “forgot your password” option. In the event that you lose your seed expression, you will also, without exception, lose access to your wallet. Save this seed phrase offline in a secure location. Simply, write it down on a piece of paper and place it in your usual spot.
4. Choose a secure password that you regularly update.
According to a study, 75% of millennials in the U.S. use the same passwords across several devices. What is the most well-known hidden term, as shocking and ludicrous as it may sound? Yes, you are correct. It’s 123456. In an independent NordVPN investigation, this secret phrase outperformed the top 200 commonly used passwords worldwide. And how long does it take for it to break? Considering everything, just a second! Imagine someone putting all of their earned cryptographic funds in a wallet that has this code word. Who is really at fault? The hardest passwords, on the other hand, are completely random ones and constitute a significant challenge for programmers. Nonetheless, in the case that you can’t remember them, you should also write them down somewhere secure.
5. Use different wallets for your investments.
Never trust just one person with your future. Think about having two dozen eggs. Which is more dangerous? Should I divide the eggs equally into two separate baskets or put all of them in one basket? Suppose the basket falls. The eggs would all crack! But what if only one of the two baskets you had fell? The same idea holds true in the area of trading cryptocurrencies.
6. Steer clear of cryptocurrency scams on social media
Imagine you’re watching a YouTube video about the most effective way to earn money from cryptocurrency trading. The manufacturer of the substance is reputable in this market, and the channel has more than 500,000 supporters. You may notice the station owner asking you to contact them via their WhatsApp/Message number so you can collaborate with them and receive double the rewards somewhere in the comments. The number is shown, and you add it to your contacts. You connect with them and are added to their “exclusive” Telegram without so much as batting an eye. Currently, you are persuaded that this is a chance that could change your life.
7. Be On Guard For Phishing Attacks
In a phishing attack, hackers attempt to mislead you into providing your user credentials on a website that appears authentic. For instance, your cryptocurrency exchange may send you an email asking you to immediately change your username and secret phrase because your account has been hijacked. Despite the fact that it’s not a true link for that trade, the website appears to be legitimate. Continually confirm that the website is the correct one and that the connection is HTTPS. Exchanging cryptocurrency stage In February 2022, a wormhole attack occurred, resulting in a loss of more than $320 million. This further demonstrates that you should never rely on storing cryptocurrency in any web-based exchange, regardless of the level of security. To manage your risks, it is wiser to store your advanced currencies in remote and online wallets.
8. Make Use Of A Secure Connection
Home office work is a blessing. You can now donate to causes while sipping on your favorite coffee at a nearby restaurant while watching from a distance. Whatever the case, this is the trick: Public WiFi is not secure, making web-based transactions from your ledger or cryptocurrency wallets difficult. Always connect with a trusted VPN when using public networks.
Read latest article: What Is Data Science?
Is the Future of Digital Wallets Safe Enough?
Advanced encryption is used by digital wallets to ensure that your payment information never leaves your mobile device. Advanced wallets are also incredibly secure because they reside inside your password-protected device and frequently only allow payments through special markers.
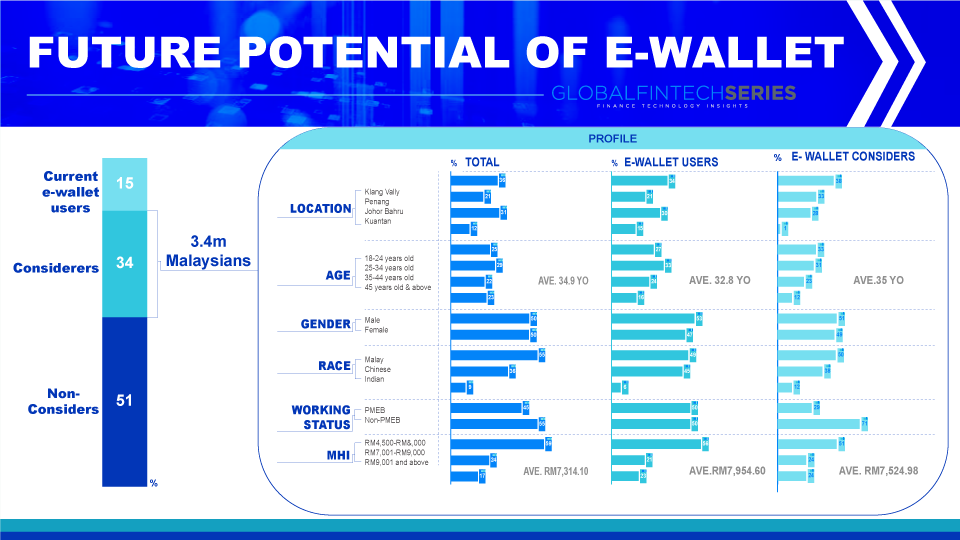
Numerous wallets also provide extra security protocols that can be used, such as two-factor validation one-time PINs. In any case, it’s wise to exercise caution. Always keep your passwords a secret, check your records for suspicious activity, and make sure you have a plan in place to disable your device in the event that it is lost or stolen.
Read: 5 Unconventional Ways To Make Money On Crypto In 2023